Lessons Learned from a DDoS Attack on My Blog
Written on
Chapter 1: The Unexpected Journey
When I launched my blog, ihateprogramming.com, I envisioned it as a minor side venture. My intention was simply to share programming tips, tutorials, and a few lighthearted jokes about the challenges of coding. However, I was taken aback when it quickly gained traction and presented a harsh lesson in cybersecurity.
The Unexpected Surge in Popularity
After securing the domain ihateprogramming.com, I published a handful of articles and shared the link with friends at my university. To my astonishment, the blog began to attract visitors beyond my immediate circle. It didn't take long for the site to experience a consistent influx of traffic, signaling that this was evolving into more than just a pastime.
An Intriguing Proposal
Shortly after my blog started gaining momentum, I received an email from an interested buyer wanting to purchase the domain. They initially offered me 300 reais, but given the traffic and potential of the site, I countered with 4,000 reais. Unfortunately, the negotiation did not end well, and the buyer was displeased with my response.
Understanding DDoS Attacks
Before I delve into the events that unfolded, let’s clarify what a Denial of Service (DDoS) attack is for those unfamiliar with the term. A DDoS attack is a malicious effort to disrupt the normal operations of a targeted server, service, or network by inundating it with excessive internet traffic. Imagine it like a highway jammed with so many cars that legitimate users can't navigate through.
The very next day after our negotiations fell apart, my blog was hit by a colossal DDoS attack. The site was bombarded with an astounding 50 million requests in a brief period. My AWS free tier couldn't cope with the sudden influx, causing my website to go offline almost instantly. To compound the situation, I received a $60 bill from AWS due to the excessive usage. It became evident that I was deliberately targeted, serving as a crucial reminder about the significance of cybersecurity.
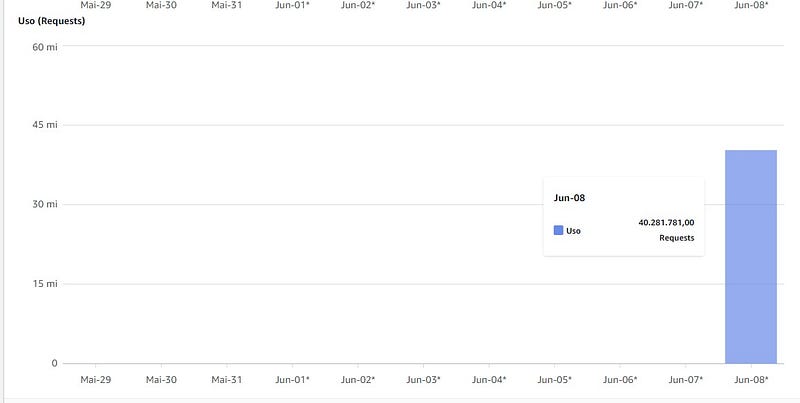
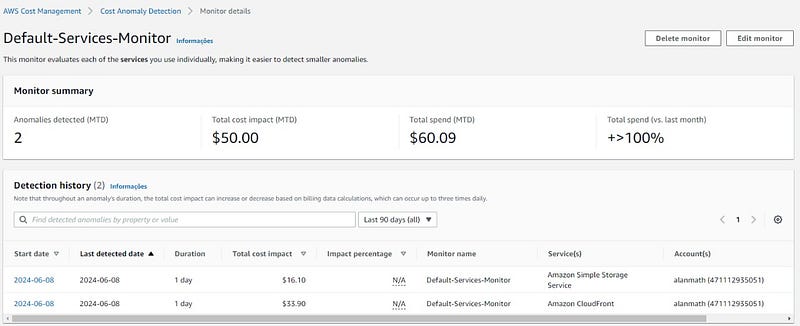
A Surprising Second Offer
Following the DDoS attack and the downtime of my blog, I received an unexpected message. This communication, as illustrated in the image above, came from an individual who claimed to have my contact information through a consultant at GoDaddy. He mentioned that he noticed my website had been offline and suggested that I might be interested in selling the domain, ihateprogramming.com.
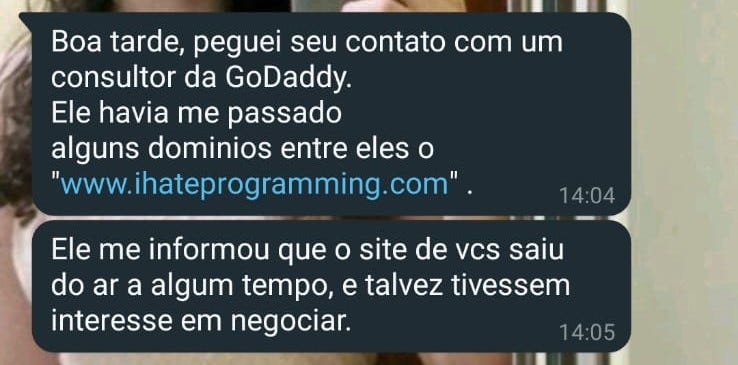
It seemed likely that this individual was the same person who had previously attempted to purchase the domain. It became clear that the attack wasn't simply a random act of vandalism but a strategic move aimed at diminishing my site's value and pressuring me into selling for a lower price. His approach was transparent: by attacking my site and causing it to be offline, he hoped to frustrate me into accepting a less favorable offer.
Chapter 2: Embracing Cybersecurity
Determined to learn from this incident, I began researching how to better safeguard my site against future attacks. Here are the key insights I gained:
- Know Your Environment: Familiarize yourself with the security features of your platform and learn how to configure them effectively.
- Implement Rate Limiting: This technique prevents a single user from overloading your server by capping the number of requests they can submit within a specific timeframe.
- Enable Web Application Firewall (WAF): A WAF helps shield your site by filtering and monitoring HTTP requests, protecting against common online threats.
- Monitor Traffic Regularly: Keeping an eye on traffic patterns can help identify unusual activities early on, potentially stopping an attack from escalating.
- Set Up Alerts for Unusual Activity: Alerts can act as an early warning system for potential attacks, allowing you to react swiftly.
- Have a Response Plan: Be prepared with a strategy for various types of attacks, including measures to mitigate them and protect your data.
- Do Not Underestimate Your Digital Footprint: Even seemingly small projects can become targets if they draw unwanted attention. Always prioritize security.
Building a More Secure Online Presence
After this experience, I rebuilt my blog with enhanced security protocols and have become increasingly vigilant in protecting my online ventures. If you're considering launching your own site or online service, make security a top priority from the outset. The internet offers numerous opportunities, but being prepared for the accompanying risks is essential.
In the video "Prepare for a DDOS Attack Before it Happens to You! - Full DDOS Deep Dive," you’ll find essential strategies to safeguard your online presence against potential threats.
In "How I survived a DDoS attack," I share my personal journey and the lessons learned from overcoming a DDoS attack.