Emergence of Purple Fox Malware: A Growing Cyber Threat
Written on
Chapter 1: Introduction to Purple Fox Malware
The cybersecurity landscape is currently facing a significant challenge with the emergence of the ‘Purple Fox’ malware. Initially identified in 2018, this worm first gained notoriety by affecting around 30,000 users through exploit kits and phishing schemes. Recent findings from Guardicore Labs indicate that a new campaign has surfaced, utilizing innovative methods that increase the malware's infection rate significantly.

As we are still recovering from the Microsoft Exchange Server breach, reports have emerged about a REvil ransomware attack on the computing giant Acer, with attackers demanding an unprecedented ransom of $50 million. Leaked documents reveal sensitive financial information, although it remains unclear whether Acer has complied with the ransom demands.
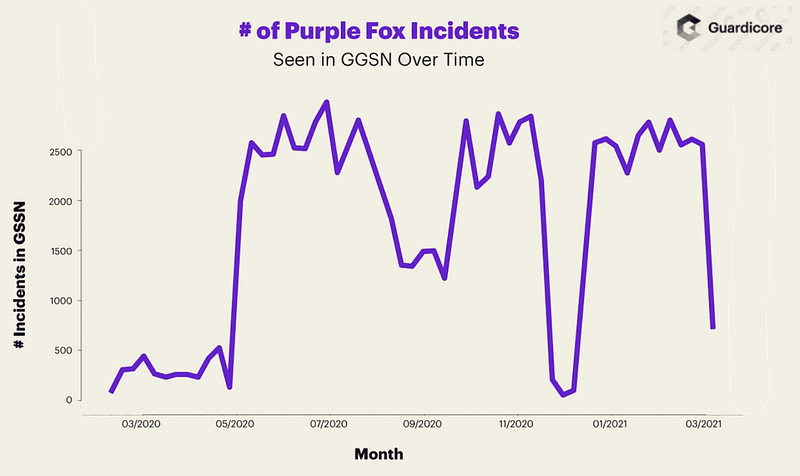
Section 1.1: Recent Trends in Malware Activity
Returning to the topic of Purple Fox, telemetry data from the Guardicore Global Sensors Network (GGSN) indicates a surge in malware activity since May 2020. Despite a brief decline from November 2020 to January 2021, the overall infection rates have skyrocketed by approximately 600%, with the total number of attacks reaching 90,000.
Subsection 1.1.1: Mechanisms of Infection
The latest wave of Purple Fox infections is primarily occurring through previously compromised systems. Many of these affected servers are operating on outdated versions of Windows Server, specifically with Internet Information Services (IIS) version 7.5 and Microsoft FTP. The malware exploits vulnerabilities in internet-facing services through various methods, including SMB, phishing-induced browser exploits, brute-force attacks, and rootkits like RIG.
Currently, Purple Fox has breached nearly 2,000 servers. Security experts note that once the malicious code is activated, it establishes persistence by creating a new service that executes recurring commands, continuously pulling Purple Fox payloads from harmful URLs.
Section 1.2: Evasion Tactics
Purple Fox employs sophisticated evasion tactics by masquerading as a Windows Update package with varying hashes. This clever strategy allows the malware’s distinct payloads to remain unlinkable during investigations. One of its payloads disrupts Windows firewall capabilities, blocking multiple ports to prevent reinfection by other malware strains. Additionally, the malware installs an IPv6 interface for efficient port scanning, generating IP ranges and initiating scans on port 445 to facilitate its spread.

Chapter 2: The REvil Ransomware Attack on Acer
The first video titled "Goat named Prince gets loose, wreaks havoc inside NE group home" humorously highlights how a mischievous goat caused chaos in a group home, showcasing the unexpected challenges faced by caregivers.
In contrast, the second video "The Darkest Minds | Official Trailer [HD] | 20th Century FOX" provides a gripping look at a dystopian world where children with extraordinary abilities are hunted down, underscoring themes of control and rebellion.
Stay updated with the latest information that matters—sign up for my mailing list.